Access Control Softwares (662)

Premier Elite V2.02 firmware is contained within the latest version of Premier Elite Flasher Interface software. The Premier Elite Flasher Interface can be used to update the Premier Elite Control Panels firmware, allowing additional features and functions to be added to existing systems.
Add to Compare
DSX WinDSX starter/update Kit consists of 1-WinDSX Software CD, 1-Tech Binder and 2-WinDSX User Guides. This version uses Microsoft Accessfor the DataBase engine. Whereas, the WinStart SQL starter/update Kit consists of 1-WinDSX SQL Software CD, 1-Tech Binder, 2-WinDSX User Guides and a USB Features Key. The WinStart SQL uses Microsoft SQL Server as the database engine.
Add to Compare
TDSi 5002-5010 is a Mifare programmer allows to control Mifare card security by specifying own sectors and keys to secure site. It can be re-configured to own requirements without any input from TDSi. It also provides a secure method for programming user cards, using a variety of methods with a secure user login function.
Add to Compare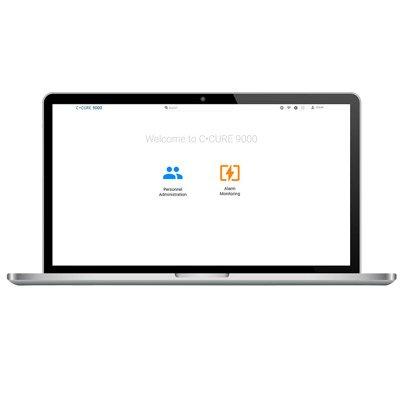
Access C•CURE 9000 from any PC with an internet browser Configure, view, and manage personnel records and credentials, and assign clearances quickly and easily with an adaptive interface Customise the appearance of C•CURE 9000 for different operators for a more simplified user interface Operator preview mode to see defined roles and responsibilities View patterns and anomalies with analytical bubble images colour-coded by priority for a dynamic visual alarm monitoring experience Smoothly transition from light to dark mode theme to reduce light reflection for optimal viewing in a dark environment Advanced search, toggle, and filtering capabilities for foolproof views Supports User Defined Fields (UDF) to customise personnel information Quickly search personnel records by name to look up card holder information Easily print ID badges for individual employees or select multiple employees for batch printing Streamlined and intuitive icon-driven user interface for an enhanced user experience TLS 1.2 secure communication to server
Add to Compare
WinDSX SQL can now utilize complex logins and passwords facilitated by Active Directory in Windows™. Operator Logins can be authenticated by Active Directory instead of WinDSX. To configure this, the WinDSX SQL Operators use the same Login Name as they do in Windows™. Their Login name is entered like always under Operator Passwords. The Operator is assigned a Password Profile but is not assigned a Password. When WinDSX SQL receives a login from an operator that does not have a password in it’s database it sends the login request to Active Directory (AD) for authentication. If AD authenticates the operator they are given access to WinDSX SQL according to the Password Profile assigned to them.
Add to Compare
After the initial download of all parameters to the system controllers, the WinDSX software keeps track of what data is changed in each location and automatically downloads only the specific changes to that location. Card Holder updates are almost instantaneous. This Fully Distributed System has speed and efficiency with its intelligent controllers. Changes that are made from a workstation are automatically downloaded to the system controllers even while additional changes are being made. The system controllers continue to operate at full capacity while the database memory allocations are increased to accommodate more doors or additional cardholders.
Add to Compare
The EventCast program will allow other software to receive event messages from the WinDSX software in near real time. These messages can be transmitted via a serial port, or via LAN using UDP. Any or all of thetransmission methods may be used simultaneously.
Add to Compare
The Two Man Rule requires that two different cardholders use their card before they can gain access to a door. This could be set up for any two card holders or it could be taken a step farther so that a card holder from Group A and one from Group B must both use their card for the door to unlock.
Add to Compare
Includes a total of 1,000 unique Approvers/Requesters Sends access requests to the owner of a specified clearance directly thereby streamlining the process Configure multiple levels of approvers and minimum number of approvers per level Define approval hierarchy Specify recurring clearance review activity Escalate missed clearance reviews Reduce workload on security personnel Empower cardholders to make access requests Entrust clearance owners with the control to approve, deny and revoke clearances Maintain security by turning company policies into automated workflows Comprehensive log for review and audit purposes Optionally configure doors to automatically initiate requests upon “access denied” events
Add to Compare
Includes a total of 1,000 unique Approvers/Requesters Sends access requests to the owner of a specified clearance directly thereby streamlining the process Configure multiple levels of approvers and minimum number of approvers per level Define approval hierarchy Specify recurring clearance review activity Escalate missed clearance reviews Reduce workload on security personnel Empower cardholders to make access requests Entrust clearance owners with the control to approve, deny and revoke clearances Maintain security by turning company policies into automated workflows Comprehensive log for review and audit purposes Optionally configure doors to automatically initiate requests upon “access denied” events
Add to Compare
PC Master allows for LAN communications to each Slave or cluster of Slave Controllers instead of just the Master Controller. This software allows a PC to emulate a Master Controller of a single location and communicate with slave panels using TCP/IP over a LAN/WAN. This is not required for typical PC to Master Controller communications using TCP/IP and a DSX LAN module.
Add to Compare
SALTO HAMS Excellence is a hotel access management software for control of hotel access and guest management. It can manage upto 16 on line doors and 40,00,000 users. Both guest rooms and back of house doors are managed in one system and it can control both off line and on line units centrally. The software is network ready.
Add to Compare
DSX can accommodate restricting and/or changing Access Levels on the card population without the need for lengthy downloads. This can be done for card control at a university that needs to shut off or restrict access to its student population during the holidays but has different time requirements for the different classes of the student population. It can also be used in Threat Level Management to change the accessibility of the Card Holders. This application is based on the new Time Zone Linking features of the WinDSX 3.7 and higher software. It requires that all controllers in the location have a 1040 processor and firmware version 3129 or higher.
Add to Compare
Includes a total of 1,000 unique Approvers/Requesters Sends access requests to the owner of a specified clearance directly thereby streamlining the process Configure multiple levels of approvers and minimum number of approvers per level Define approval hierarchy Specify recurring clearance review activity Escalate missed clearance reviews Reduce workload on security personnel Empower cardholders to make access requests Entrust clearance owners with the control to approve, deny and revoke clearances Maintain security by turning company policies into automated workflows Comprehensive log for review and audit purposes Optionally configure doors to automatically initiate requests upon “access denied” events
Add to Compare
Additional 10,000 Approvers/Requesters Sends access requests to the owner of a specified clearance directly thereby streamlining the process Configure multiple levels of approvers and minimum number of approvers per level Define approval hierarchy Specify recurring clearance review activity Escalate missed clearance reviews Reduce workload on security personnel Empower cardholders to make access requests Entrust clearance owners with the control to approve, deny and revoke clearances Maintain security by turning company policies into automated workflows Comprehensive log for review and audit purposes Optionally configure doors to automatically initiate requests upon “access denied” events
Add to Compare
MEET MANAGEMENT SOFTWARE (MMS) is a PC software application especially designed to work as a management and administration centre and optionally perform installer functions.The MEET MMS system is a software application with multiple uses which, firstly, permits the installation and commissioning of the system and, secondly, is the ideal tool to manage the installation in terms of security, comfort and communication for the residents.It performs the following functions: Message send to monitors Management of alarm warnings and panic calls It performs configuration functions Communication event log Access control event log and management Alarm event log and configuration Face recognition image upload Online devices monitoring Users and devices database management Device configuration push
Add to Compare
Additional 100,000 Approvers/Requesters Sends access requests to the owner of a specified clearance directly thereby streamlining the process Configure multiple levels of approvers and minimum number of approvers per level Define approval hierarchy Specify recurring clearance review activity Escalate missed clearance reviews Reduce workload on security personnel Empower cardholders to make access requests Entrust clearance owners with the control to approve, deny and revoke clearances Maintain security by turning company policies into automated workflows Comprehensive log for review and audit purposes Optionally configure doors to automatically initiate requests upon “access denied” events
Add to Compare
Small to medium upgrade Sends access requests to the owner of a specified clearance directly thereby streamlining the process Configure multiple levels of approvers and minimum number of approvers per level Define approval hierarchy Specify recurring clearance review activity Escalate missed clearance reviews Reduce workload on security personnel Empower cardholders to make access requests Entrust clearance owners with the control to approve, deny and revoke clearances Maintain security by turning company policies into automated workflows Comprehensive log for review and audit purposes Optionally configure doors to automatically initiate requests upon “access denied” events
Add to Compare
Up / down loading software Provides a complete way of monitoring events reported from a panel to a central receiving station Choice of Access or SQL databases Networkable with an unlimited number of operators Flexible report creating feature Programmable dedicated event resolution keys from F1-F12 Programmable different access levels for each operator Programmable audible alarms for each event group Programmable expected open/close schedule per account Up to 9 levels of maps per account Supports SK Extended, MLR2, Ademco 685, and Pyronix IP automation protocols
Add to Compare
Medium to large upgrade Sends access requests to the owner of a specified clearance directly thereby streamlining the process Configure multiple levels of approvers and minimum number of approvers per level Define approval hierarchy Specify recurring clearance review activity Escalate missed clearance reviews Reduce workload on security personnel Empower cardholders to make access requests Entrust clearance owners with the control to approve, deny and revoke clearances Maintain security by turning company policies into automated workflows Comprehensive log for review and audit purposes Optionally configure doors to automatically initiate requests upon “access denied” events
Add to Compare
Manager First can be used to keep other subordinate issued cards from gaining access to the building when the manager is not on site. Certain access levels would be disabled until a manager arrives and uses their card thereby enabling the access levels of the subordinates.
Add to Compare
DSX can accommodate keeping a door locked until a card holder is granted access at that same or other door. This prevent s a door(s) that normally unlocks via Time Zone from unlocking on a day when no Card Holders come in such as on a “S now D ay ”. There are several variations to this which are covered below. This application is based on the new Time Zone Linking features of t he WinDSX 3.7 and higher software. It requires that all controllers in the location have a 1040 processor and firmware version 3129 or higher.
Add to Compare
Hazmat Lockdown accommodates the quick lockdown of a system required for Hazmat alerts. The Lockdowns occur without the need of programming or lengthy downloads. Hazmat Lockdowns typically secure all the doors in an area or the entire facility not allowing anyone or just particular personnel access in or out. This application is based on the new Time Zone Linking features of the WinDSX 3.7 and higher software. It requires that all controllers in the location have a 1040 processor and firmware version 3129 or higher.
Add to Compare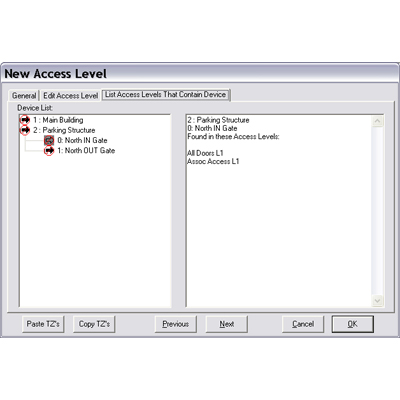
At a time when Accountability and Reporting are an ever increasing requirement, DSX is creating solutionsthat will provide the information needed. Reader (Device) Locator in Access Levels When defining a new access level or editing an existing one there is a new tab that will show the user which access levels contain a selected device. This data is displayed in a text box that can be copied and pasted into any other application for storage, printing, or emailing. This new View streamlines the effort in locating all of the access levels that contain a specific reader.
Add to Compare
DSX DSX-HSCS software provides continued availability of system communications and control through the implementation of primary and backup communication server PCs. Available only with WinDSX SQL the Hot-Swap Supervisor runs on the backup comm server and monitors the primary comm server. When the primary fails all communications are redirected to the backup comm server.
Add to Compare
Additional 1,000 Approvers/Requesters Sends access requests to the owner of a specified clearance directly thereby streamlining the process Configure multiple levels of approvers and minimum number of approvers per level Define approval hierarchy Specify recurring clearance review activity Escalate missed clearance reviews Reduce workload on security personnel Empower cardholders to make access requests Entrust clearance owners with the control to approve, deny and revoke clearances Maintain security by turning company policies into automated workflows Comprehensive log for review and audit purposes Optionally configure doors to automatically initiate requests upon “access denied” events
Add to Compare
The WinDSX HVAC After Hours Zone Control feature can be used in multi-tenant buildings to control and monitor the after hours use of heating and cooling systems in each tenant space. This control gives the administrator the ability to define the amount of extra consumption that each tenant is responsible for. This information can be used to bill the tenants for the correct amount of usage. The HVAC Control feature operates in conjunction with all other WinDSX features simultaneously.
Add to Compare
Within WinDSX, Linking is a flexible and powerful feature. Linking to Inputs controls their armed state. Linking to Outputs controls their on/off state. Linking to Time Zones overrides their schedule either on or off. Inputs can link to Inputs, Outputs, and to Time Zones. Outputs can link to Outputs, Inputs, and to Time Zones. Virtual Outputs are Outputs that do not physically exist but can be used in linking schemes. Outputs that do not physically exist are not supervised but the system manipulates them as if they were actually there. Their status is displayed in Workstation and they can be used in conjunction with Time Zones and Linking.
Add to Compare
DSX Alternate Time Zone software application an quickly disable one Time Zone and/or enable another through Time Zone Linking. There are times when an application calls for multiple schedules to control cards or door locks with the ability to switch from one schedule to another without any programming or Time Zone reassignment. This action could be a manager card being used at a reader that switches a door from one locking schedule (Time Zone) to another or the clicking on an Output Icon in the Workstation program.
Add to Compare
DSX Drug Test Selector assists users in the random selection process of card holders to be drug tested. It can be used to deactivate random card holders. The program is copied into the WinDSX folder on the PC where it is to be used. The card can reactivated by simply editing the card record and changing the deactivate field to a future date and saving the card.
Add to Compare
The DSX-SIO L85 Wireless Interface is an interface based on Soft I/O (SIO) that can be used for Wireless Equipment Integration. The SIO L85 leverages Software and Virtual Hardware to accommodate Wireless Locks and Readers. Hundreds or even thousands of Wireless devices can be installed through multiple deployments of L85. Wireless devices are a powerful addition to the DSX Access Control System. The DSXSIO L85 sets the stage for even more flexibility providing a fully integrated solution of both hardwired and wireless readers and locks.Wireless Devices are well suited for applications calling for a large number of doors such as College Dorms or any place where traditional hardware is almost impossible to install due to architectural constraints. High numbers of Low Security Doors with the need of supervision and online management is a strong point for the DSX-SIO L85.DSX-SIO L85 becomes part of any DSX Location through the use of IP/Gateway or a traditional network of controllers to include at least a Master Controller. The SIO L85 then communicates with up to 126 wireless devices mapping those wireless devices to Virtual Devices, Inputs, and Outputs defined in the WinDSX program. There is little difference in the WinDSX program between the hardwired and wireless devices and most operators won't know the difference. Just about any feature in WinDSX also applies to the wireless devices connected through SIO L85.
Add to Compare
DSX Threat Level Management software application is based on the new Time Zone Linking features of the WinDSX 3.7 and higher software. It requires that all controllers in the Location have a 1040 processor and firmware version 3129 or higher. Threat Level Management can go a bit further reconfiguring the system by Securing Ou tputs (locking doors), restricting Device (reader) access, altering Access Levels, arming Input points, enabling Image Recall and more.
Add to Compare
Hazmat Lockdown accommodates the quick lockdown of a system required for Hazmat alerts. The Lockdowns occur without the need of programming or lengthy downloads. Hazmat Lockdowns will typically secure all the doors in an area or the entire facility not allowing anyone or just particular personnel access in or out.
Add to Compare
Premier Elite V2.02 firmware is contained within the latest version of Premier Elite Flasher Interface software. The Premier Elite Flasher Interface can be used to update the Premier Elite Control Panels firmware, allowing additional features and functions to be added to existing systems.
Add to Compare
KeyStar increases the existing security of users master key systems by managing data by way of classification. The software covers all basic requirements (personnel and key data processing, allocation confirmation and listing of allocated keys) and its database can be produced using SATELLIT Planner (for EVVA customers with specific requirements).
Add to Compare
Data access – free access to existing EVVA system data Import and export – simply import locking charts from Excel and export them from AccessDesigner Version history – older system versions remain backed up as a result of automatic data backups Locking chart checks – plausibility check of the locking chart prior to ordering Data backups – your data is safe here – automatic data backups at EVVA’s own data centre Product configurator – order codes are always up to date in the software – makes transparent orders so simple
Add to Compare
SALTO HAMS Connected is a hotel access management software for control of hotel access and guest management. It can manage unlimited on line doors and up to 40,00,000 users. Both guest rooms and back of house doors are managed in one system and it can control both off line and on line units centrally. The software is network ready.
Add to Compare
SALTO Pro Access 100 access control software can manage upto 4 on line doors and 100 users. The features allow to program access time zones for each user, take into account different company calendars, obtain audit-trails from the door to see who has passed through it, and it includes special functions like automatic changes of the door status, anti pass back and relay management (i.e. elevators control). It can manage large numbers of door installations, and as most access related information is written on the credential, the management of the doors becomes, in cases, a management of the credential. By simply updating the badge, most access related authorisations of the users can be changed, including adding/deleting doors, time zones, calendars etc.
Add to Compare


