Access control systems & kits (1,099)

UltraMatch series products has a stylish design and reliable performance. Adopting BioNANO algorithm, the system provides the most accurate, stable, and quickest iris recognition while delivering high-level security in biometric enrollment, individual identification, and access control. Iris recognition system can identify and authenticate users accurately and is not affected by outside environmental conditions. A web based software and a PC version management software allow clients to manage the system easily. Iris SDK is available to developer and integrator for developing identity management applications or easy integration and expansions to existing security system. Depending on its high accuracy, the terminal is ideal for high-level security applications, such as Border Protection, Pharmaceutical & Healthcare or Jails.
Add to Compare
W1 Pro is the new generation fingerprint time attendance terminal features based on Linux platform. W1 houses 2.8-inch color LCD with rich colours and visibility that displays intuitive GUI that is easy to understand and self-explanatory. Full capacitive touch keypads along with touch optical fingerprint sensor will offer convenient operation experience and improve the practicality of the wet and dry fingerprint.
Add to Compare
Linux platform provides a safe and stable performance Comparison time less than 0.5s Ergonomic design with new touch keypad provides a better user experience TCP/IP\WiFi\Bluetooth\4G are provided to satisfy different needs Provide 1 relay for belling and connecting to Access Control system The battery ensures the wireless application New material that makes it more appealing and durable Bigger and brighter 3.5 inch color display Fast & easy installation through a wall-mounted panel Ease the experience of user by brand new UI design
Add to Compare
Introducing the new eMerge™ E3 Series from Linear: a powerful Access Control platform delivering best-in-class value for businesses of any size: Monitor and manage the system via the LAN, WAN, WWW, from a PC, laptop, or mobile device (tablet, smart phone) Delivers a lower Total Cost of Ownership (TCO) by eliminating future system upgrade and reconfigure costs, and reducing daily operating costs Rapid and hassle-free system expansion via License Key – single platform controls a growing number of connected systems and devices Replaces PC-based systems with open architecture solid-state hardware that is easier to install, integrate and use One System for 1 - 360 Doors The eMerge E3 Series is a single platform that suits virtually every application and operation size. Fully scalable at the touch of a button, users can select models based on their current access control needs, and upgrade as their business grow with the purchase of a License Key -- no data conversions, no hardware changes, just the right system, at the right price. eMerge Essential: 1 door/2 readers; out-of-the box expansion to 4 doors/8 readers eMerge Elite 36: 36 doors/72 readers eMerge Elite 64: 64 doors/128 readers eMerge Enterprise: 4-360 doors/720 readers
Add to Compare
These full-featured, self-contained hardware/software access systems are perfect for commercial, industrial, banking, medical, retail, hospitality, and other businesses where users need to secure their facilities, manage access of personnel, create and analyse reports, and monitor the system remotely from any web browser.
Add to Compare
Identification Modes: Face, card, password multiple ways to choose, convenient, flexible and safe to use Attendance Status: User-defined function keys to switch attendance state, meeting multiple identification needs Card: Standard EM, Optional Mifare Open the Door Remotely: Remote opening through network and software management Security: Security incident monitoring and alarm Access Control Interface: Support Relay Output, Wiegand26/34 Input and output, magnetic, etc. Infrared Sensing: Infrared sensor activation U Disk Download: Support U disk, user information record backup And firmware upgrade Multi-language: Support Global Multilingual Display
Add to Compare
Clear and easy to read 2-Line OLED display Programmable backlight brightness suitable for bright or low-light environments Slimline surface mount design Stylish design and neutral colours will look great in any environment Design style compliments the PrismaX Keypad (colour screen model) Backlit rubberised keypad provides a user-friendly tactile feel Eight LEDs provide area status, door functions, alarms and other conditions via programming options Instant help text available anytime, at the press of a key Multilingual firmware as standard (12 languages) Four ‘arrow’ keys provide quick and convenient access to menu options Zone inputs and auxiliary outputs provided for connection of local I/O devices Programmable panic key and duress option Built-in module locater buzzer Tamper monitored housing Compatible with Integriti, Inception & Concept 4000 Systems
Add to Compare
New generation touchless solution for the people to access control on the entrance or record time attendance and simultaneously check mask-wearing without having to touch a terminal or gate. Built-in IR and visual cameras integrated with Anviz’s unique BioNANO algorithm to produce the best in class live face recognition performance.Equipped with a 5" IPS touch screen. Register up to 10,000 users for dynamic face authentication. Recognition distance up to 1.5 M with matching speed < 0.3s by 1: 10,000. Optional battery backup, specifically designed to work consistently in unstable power supply environments, such as Construction sites,Manufacturing, Schools and buildings in countryside, etc.
Add to Compare
Easyprox compact is an all-in-one battery powered lock and access control system that's perfect for securing internal doors - especially those that don't have an accessible power supply. The system is exceptionally easy to install because its control electronics are housed within the reader and a battery power source replaces mains wiring. Consequently installation times, costs and on-site disturbance are greatly reduced. Battery power sourceElectronics housed within readerNo mains wiringEasy to install (less than 40 mins in some cases)Everything included in the boxSpare battery packs availableExternal contacts in case batteries run outAnother reason why Easyprox compact is such great value for money is because everything required to secure a door is included: reader/control unit, handle, lock, battery pack and fixings etc. The unit is supplied with a tubular mortice latch and is surface mounted. The system also has an anti-shim plunger that prevents entry using credit cards. The use of energy saving technologies guarantees a huge battery life of five years based on 15 daily uses. Easyprox compact uses standalone tokens that are compatible with Paxton Access' other standalone systems. Introducing it to new and existing access controlled sites is therefore a convenient and economical solution. The inclusion of Easyprox compact as part of a larger system can help to make your tender applications even more competitive. Offering the same conveniences as its token counterpart, Easyprox keypad controls entry by way of a code (or PIN) and will be available soon.Applications:Halls of residenceClassroomsDormitoriesMeeting rooms/officesStore roomsCupboardsDisplay cases/stock rooms
Add to Compare
QR Codes Verification - Supports all EU countries QR codes and quickly verify EU Digital COVID Certificates via an app on your phone, or paper versions are also available. Security and Data Protection - Keeps visitor and user confidentiality without storing any data after scanning the GreenPass QR Code. Great User Convenience - FaceDeep 3 Series QR provides the user convenience with a 5'' touch screen and it can connect Anviz CrossChex Cloud software to check access and punch records from anywhere, anytime. Multi - Technology - FaceDeep 3 Series QR provides strong and safe touchless QR codes and face recognition technology to let users go cardless by using QR code scanning or faces as credentials. FaceDeep 3 IRT QR with Body Temperature Detection technology, specifically designed for simultaneous personnel access authority. Various Applications - FaceDeep 3 Series QR can be used in many practical scenarios, including visitor management, hotel, business organizations, small and medium enterprises, stadiums or public events.
Add to Compare
The new Linux based 1Ghz processor ensures the 1:3000 comparison time less than 0.5 second Your mobile device will be the key with bluetooth function and you can realize shake opening with ekey APP. The WiFi function ensures power on to work, and realize the flexible installation of the device. The standard IP65 design ensures the the complete outdoor application of the device The touch active sensor ensures the quick response for each detection and saving the total power consumption of the device. The Webserver ensures the easily quick connection and self management of the device
Add to Compare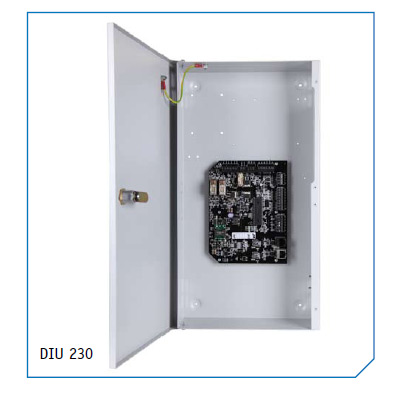
The DIU 230 delivers power and Ethernet communications via CAT5/6 Ethernet cable, eradicating the need to provide local mains power at the door. When combined with the AC2000 product range, the DIU 230 offers a complete IP-based access control solution.The DIU 230 has an output of 2 Amps, providing power to support up to 2 complete door sets (consisting of entry and exit readers, heavy duty Maglock, door holder, sounder and strobe). The DIU 230 also features:Battery backup allows continued door functions even with loss of communications to host.Tamper alarm inputs on board.Can be used in conjunction with the eDCM300 series of door controllers.The DIU 230 provides a cost-effective way of bringing power to the door. The DIU 230 installation is classed as low voltage and can be completed by security integrators and IT network installers without the expense of an electrician or electrical contractor.
Add to Compare
Linux platform & Dual 1.0GHz CPU to provide a safe and stable performance Comparison time less than 0.5s Ergonomic design with new keypad provides a better user experience AFOS the lastest fingerprint sensor, touch on activation infrared, optical imaging technology Standard WiFi, Optional 3G Provide relay output for standalone Access Control Support Wiegand, RS485 and USB-host extended communication HD and brighter 3.2 inch color display Ease the experience of user by brand new UI design PoE(Power Over Ethernet) fast & easy installation
Add to Compare
Morse Watchmans KeyWatcher 8 Key Module is an electronic key cabinet system. It contains 8 SmartKey locations. and is perfect for situations where there are multiple locations within a building or campus that need only a limited number of keys managed.
Add to Compare
Linux platform & Dual 1.0GHz CPU to provide a safe and stable performance Comparison time less than 0.5s Ergonomic design with new keypad provides a better user experience Standard WiFi, Optional 3G Provide relay output for standalone Access Control Support Wiegand, RS485 and USB-host extended communication HD and brighter 3.2 inch color display Ease the experience of user by brand new UI design PoE(Power Over Ethernet) fast & easy installation
Add to Compare
Linux platform provides a safe and stable performance Comparison time less than 0.5s Ergonomic design with new touch keypad provides a better user experience AFOS the lastest fingerprint sensor touch on activation infrared, optical imaging technology TCP/IP & WiFi are provided to satisfy different needs Provide 1 relay for belling and connecting to Access Control system RS232 interface can be connected to a Time & Attendance printer New material that makes it more appealing and durable Bigger and brighter 3.2 inch color display Fast & easy installation through a wall-mounted panel Ease the experience of user by brand new UI design
Add to Compare
The AC-2010 Proximity Clocking Terminal is designed for time and attendance management in KeyMaster Pro or KeyMaster Lite access control systems. It is compatible with Controlsoft AC-400x, AC-4100 and AC-310x system controllers. Key features include an integrated proximity reader, a keypad, LCD screen, digital I/O capability, and support for an external Wiegand card reader. KeyMaster Pro™ 3.1 & KeyMaster Lite™ 3.0 support.
Add to Compare
The single door access module is designed to provide an interface for a single reader head along with the required inputs and outputs for the control and monitoring of a single door. The module is supplied as a PCB only and may be incorporated into any suitable existing enclosure with another LAN module or an optional external power supply. The versatile hardware and software design allows Magnetic Swipe or Wiegand Reader formats to be configured. Simple programming options allow door access control to be integrated with area on/off control where required.
Add to Compare
Elegant slimline surface mount design Full colour LCD backlit screen Large – easy to read text Four arrow keys provide quick and convenient access to options in the graphic interface menu Tamper monitored housing Light sensitive auto-dimming brightness for LCD, Keypad and LED’s Back-lit rubberised keypad provides a user-friendly tactile feel Local temperature display 8 LED indicators for Area status display Instant help text available anytime, at the press of a key Programmable panic key and duress option Compatible with Integriti Systems only Custom Logo option for standby screens
Add to Compare
The E3-Series embedded browser-based network appliances make advanced security technology reliable and affordable for any entry level access control application. Both the Essential and Elite can be seamlessly scaled up, via software keys, to other eMerge E3-Series systems providing increased door and reader capacity, enhanced features, and higher level capabilities.These full-featured, self-contained hardware/software access systems are perfect for commercial, industrial, banking, medical, retail, hospitality, and other businesses where users need to secure their facilities, manage access of personnel, create and analyse reports, and monitor the system remotely from any web browser.
Add to Compare
Linear prox.pad plus integrated proximity reader and controller with keypad. The prox.pad plus when used on it’s own provides standard access control functionality with the use of it’s two relays and two inputs for request to exit and door position, and enhanced system functionality when used with Hub Manager Professional software. The software allows the management of people and doors through easy to create reports and step by step wizard assisted expanded feature functionality. The software can communicate to the prox.pad plus either through a 485 connection, or on a LAN/WAN using the SEG-1 TCP/IP communication device.
Add to Compare
Linear prox.pad wiegand 125 kHz proximity reader with keypad is a stand alone proximity reader and keypad that can be directly mounted to a single-gang electrical box or to most flat surfaces. The prox.pad provides standard access control functionality with the use of its two relays and two inputs for request to exit and door position. By utilising the proximity reader and keypad together, a higher level of security is achieved by requiring both to grant access. The prox.pad can be used for stand alone access control, or used as a reader for IEI access systems or most Wiegand systems. The proximity reader is capable of being mounted up to a maximum of 10 feet away from the prox.pad.
Add to Compare













